Business Impact Analysis (BIA) is a fundamental first step in developing a port Business Continuity Management (BCM) system. It focuses on identifying the critical parts of port assets and operations that could be impacted and prioritizing BCM to protect these critical parts. In addition to a general BIA which incorporates all its assets and operations, a port can also focus attention on specific services, processes, and activities supporting areas of key revenue flows. Risks need to be prioritized as not all risks can be tackled simultaneously, and for some risks, it would not be cost effective.
Ports should conduct a BIA, among others, to:
- Quantify the impact a disruption will have on a port's ability to function over time;
- Enable informed prioritization of port recovery in the event of a disruption;
- Justify current and future resilience-building investments as well as expenditure on recovery strategies; and
- Enable the identification of critical dependencies (e.g. departments, suppliers, processes, applications, infrastructure, etc.).
When conducting a BIA, ports should consider the following elements:
- Interdependencies between operations, functions, and processes (both internally and externally).
- Business functions and operations, processes and IT applications that need to be recovered, and in which order of priority.
- Key personnel required to help the port recover and resume operations and activity.
- Standard operating procedures, or manual workarounds.
- Alternate sites or technology requirements for support staff (e.g. the ability to work remotely during a pandemic).
- Compliance requirements or regulatory obligations.
- Location of essential records for relevant activity and operations and potential backup records and files.
- Consideration of external vendors and other third parties, including hinterland operators.
- The time during which the port can sustain without a key service such as IT, known as recovery time objective.
- Security of locations where IT servers are operating.
As part of the process, creating a central repository of infrastructure information can be useful, and may include: (i) location data – latitude and longitude of the port, height above sea level, and linkages with other infrastructure; (ii) data on remaining useful life; (iii) relevant structured finance indicators from project finance documents (e.g. capital expenditures, maintenance, and operations costs); and (iv) a survey of damages resulting from past events and the associated costs. Information about key hinterland stakeholders such as logistics hubs and critical locations of key third-party providers is also important to gather as part of this process.
BIA outputs and results are generally presented as written reports and diagrams, which include:
- A list of interdependencies (both internal and external) between functions, operations, and processes within the port, as well as in connection with hinterland and terminal operations.
- A list of business operations, functions, processes, and IT applications by recovery priority.
- Key metrics are provided, such as maximum tolerable period of disruption (MTPD), recovery time objective (RTO), recovery point objective (RPO), for each critical operation/process/activity.
- Documentation relating to critical operations and processes. Printing out physical copies of the most critical documents should also be envisaged. Contact information for critical personnel should also be included. Software solutions can help in making this data available more quickly and automating some of the processes. However, they themselves need assessing for resilience.
- Documentation regarding compliance, financial and regulatory concerns, and reporting requirements.
- Documentation regarding, for example, manual workarounds, alternate sites, and technology needs.
- Critical contracts and service level agreements (SLAs) with suppliers and key port subcontractors.
- For critical IT applications, recovery time objectives (i.e. how long the port can be without the application), recovery point objectives (i.e. how much data the port is willing to lose), and backups of the port's vital electronic records.
- Lists of key personnel and planning for cross-training relating to critical functions and operations.
After port senior management and leadership endorse the BIA results, the port can start developing a port-wide Business Continuity Management (BCM) system. This requires the involvement of relevant port stakeholders and functional departments and operational units, including terminal operators, hinterland operators, local authorities and the government.
Some questions that need to be addressed as part of the BIA implementation process include whether the port can perform certain critical business processes and operations from an alternative location (or remotely) when the existing location becomes unavailable, and whether it should divide functional teams and allocate them to various port buildings to ensure that when one facility becomes unavailable, it does not also bring an entire function down, i.e. be situated in multiple smaller office buildings over one larger one).
The implementation process also requires addressing offsite requirements, cloud back-ups, or secondary data centres for crucial electronic data or paper records and whether the port can procure "on-demand" space or technology capacity in advance. Another issue to consider is whether the port faces risks that are too costly to mitigate effectively. A "do nothing" approach is not always advisable, but in certain circumstances, it may be the least worst option.
The BIA should be updated at least annually. Updates will also be required if a port has experienced new or altered operations or facilities, new key business processes or functions, turnover in key staff members (e.g. core business continuity team members), major IT application changes, or supplier changes. These changes can expose the port to new risks, including financial risks. Ideally, this update and maintenance process should be embedded in other relevant processes. For example, suppose a port has a checklist relating to the setting up of a new IT system. A note could be added to the list recommending or instructing to contact the port's business continuity team before deploying the system.
HINT
- BIA must be appropriately sized and targeted for the port before it is initiated. It should not be overly complex or overwhelming. If it cannot be carried out efficiently, stakeholders may lose interest in the exercise.
- Port services generating the largest share of revenue or which disruption could result in significant negative impacts are likely to be the critical services that the port needs to prioritize. These priority services should be integrated while considering several disruption perspectives such as financial, operational, reputational, customer and supplier, environmental, and employee impacts. It may also be appropriate to consider a broader economic impact model, such as the country or hinterland that depends on the port.
- BIA can also be considered from the risk attachment theory angle. Risks are generally defined in relation to the effect of uncertainty on objectives set. Risks can have an impact on a port's corporate objectives as well as on key dependencies, core processes, and stakeholder expectations. This is called "attachment of risk", and ports can map out how risks are attached to each of these elements to fully analyze their impact. "Risk attachment" comprises:
- Key dependencies: Internal or external elements required for achieving ports' objectives.
- Core processes: A collection of activities that deliver a specific stakeholder expectation, e.g. a successful operation of the ship-to-shore cranes.
- Stakeholders: Groups of individuals with a stake in the port, or are affected by the port's actions and decisions (e.g. port authority, terminal operators, port employees, investors, suppliers, carriers, shippers, public authorities and the broader community).
In addition to a BIA, risks can also be mapped using a risk severity and probability matrix. It benefits from a consensus approach involving individuals who are knowledgeable about the risks. It is important to note that this approach can also be extended to cover suppliers and other relevant third parties. The aim is to develop appropriate responses based on the probability and severity of the risk event. In addition, it helps ensure that risks receive differentiated management attention, and allocated resources according to their relative resilience importance.
Four risk areas are set out in the matrix below (figure 5):
- Low severity/low probability risk: These do not necessarily require BCP. They can be addressed during normal day-to-day operations.
- Low severity/high probability risks: These have a strong likelihood of occurring. The appropriate action here is to have a BCP to mitigate these risks.
- High probability/high severity risks: These require detailed business continuity and crisis management plans. These plans should focus on reducing the severity or probability.
- High severity/low probability risks: These occur rarely but have serious consequences when they do. This scenario also requires business continuity and crisis management planning.
Figure 5: Severity and probability matrix
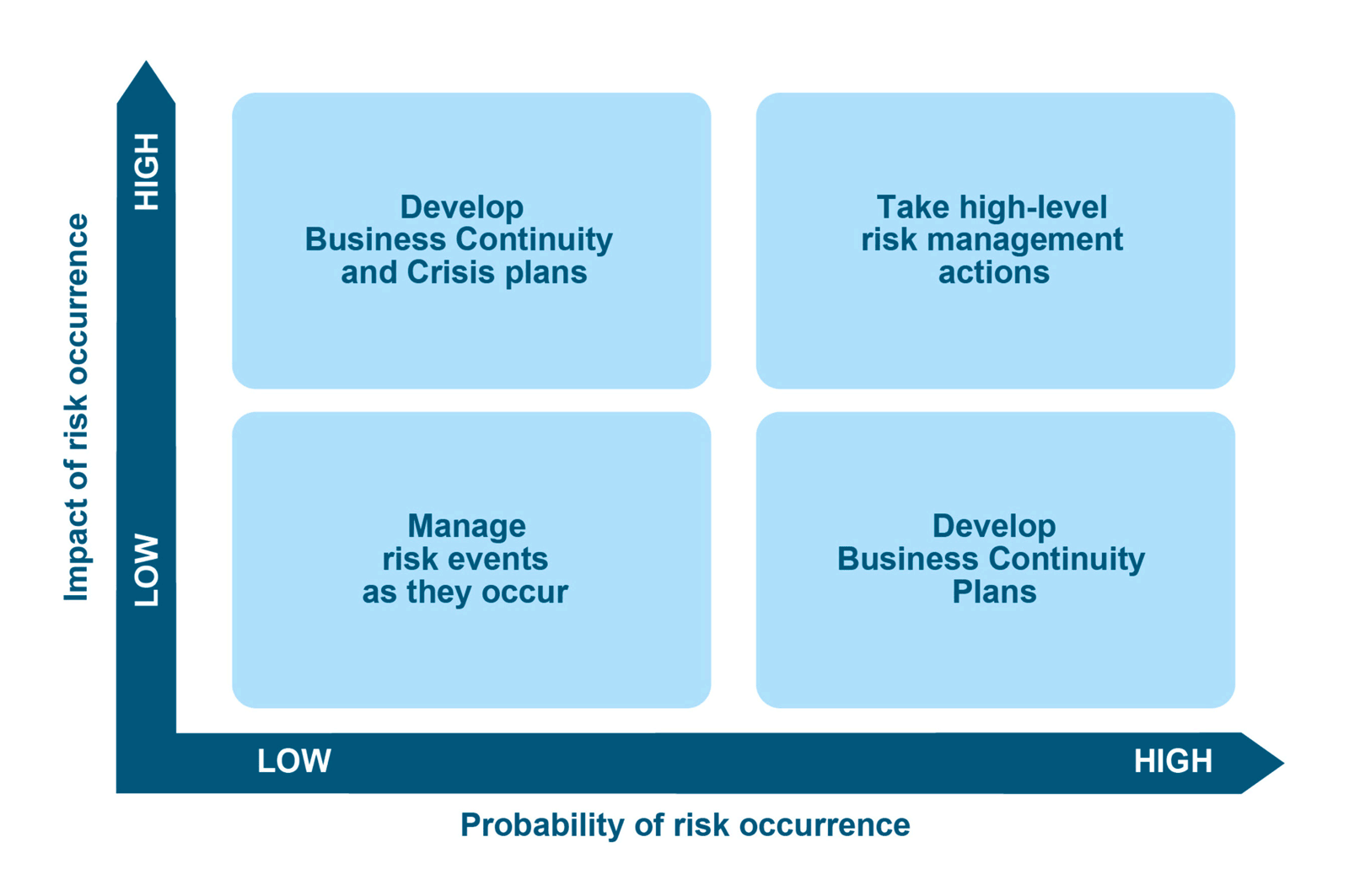
Source: Elaborated by the authors based on various sources including the Institute of Risk management and Business Continuity Institute.
Heat maps, along with the mapping matrix, have formed part of risk management for many years. There are many derivations of heat maps, but they generally follow a common approach, as featured in figure 6. BIA helps determine where risk sits on this chart. The port determines the parameters for defining the severity of the impact and likelihood of a risk to occur, bearing in mind its risk appetite and risk tolerance.
Figure 6: Heat map
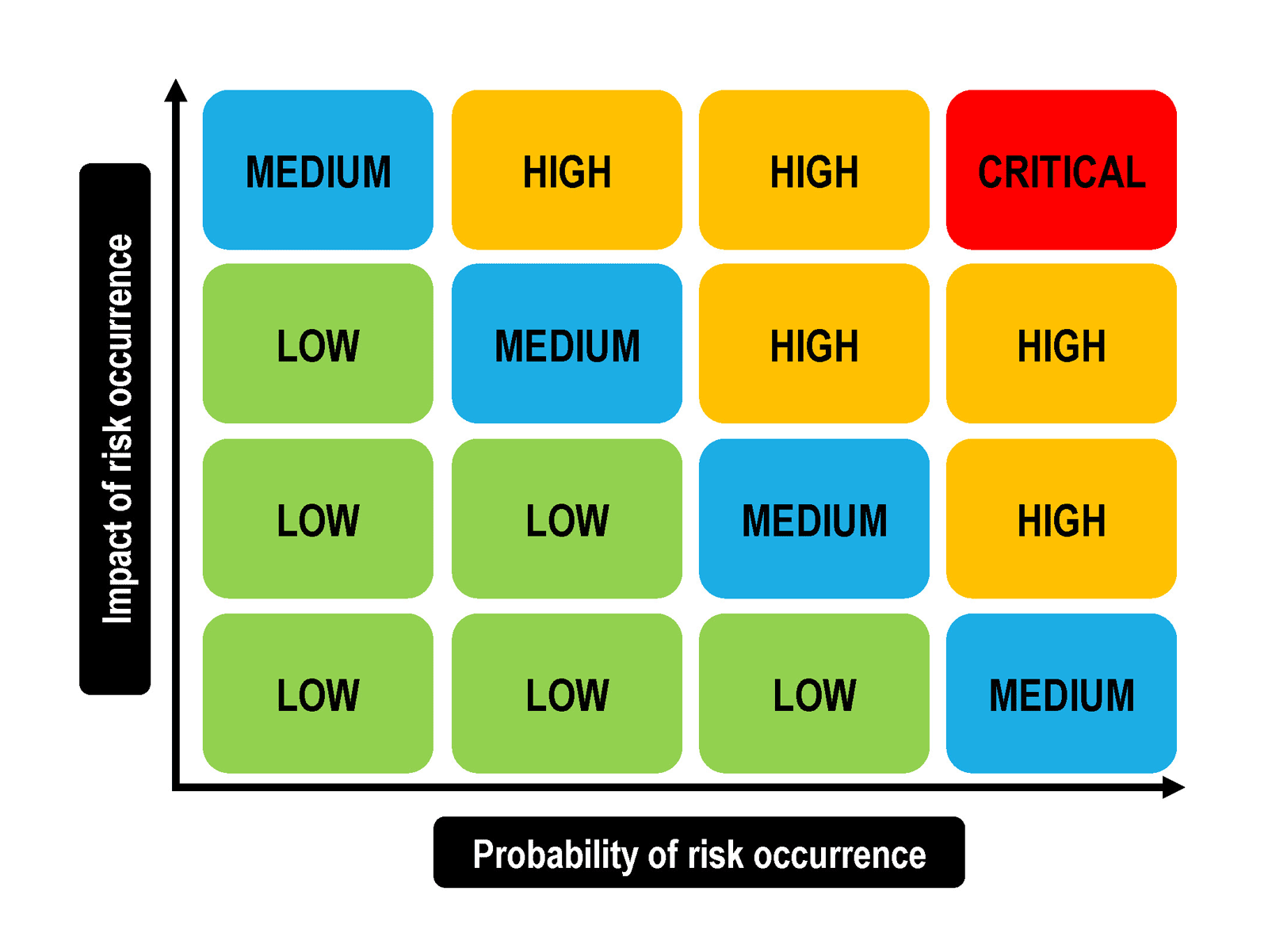
Source: Elaborated by the authors based on various sources including the Institute of Risk management and Business Continuity Institute.
Severity is usually measured in terms of the financial impact and other impacts to, among others, loss of life and damage to infrastructure or the environment. The financial measure provides a common measure that can be used as a basis to justify any risk management efforts. Likelihood refers to the probability that a disruptive event might occur.
Both the heat map and severity matrix present outputs that provide alternatives and options on how to visualize risks, their likelihood, as well as potential impacts. They can help ports to determine where they should focus their risk management efforts, strengthen their resilience, and champion greater preparedness in the face of shocks and disruptions.
HINT
- Each approach involving the identification and assessment of risks will provide results and insights that can be presented in an output/document and serve as important guidance. In some cases, such outputs of risk assessment or identification process may not always be valid or reliable, especially when it comes to predicting risk events – the probability or likelihood of the event can be underestimated.
- Validity refers to an indicator or model fulfils its intended objective. In risk management, validity addresses whether the tool is fit for purpose.
- Reliability refers to how a tool, technique or methodology is consistent across its application and usage. A watch could measure time (it has validity), but it could become inaccurate as its battery wears down (it is no longer reliable). Something that is reliable means that we have confidence in its use across time. Over or under specifying the variables to include in a risk model can also be problematic. If port risk measures or indexes are too sensitive, they may raise a flag when no unusual risks exist. By contrast, if the risk measure is not sensitive enough to detect changes, or if the model excludes the right factors, it may not notice the fact there is a likely risk event. When considering the best approaches for ports to employ when identifying and assessing risks, this should be kept in mind.
