The diffusion of IT for communication, managerial and operational considerations has pervaded the maritime industry. Even if the industry tended to be paper-intensive, the COVID-19 pandemic presented an urgent opportunity to digitalize transactions. However, the concurrent growing level of digitization and reliance on information systems has opened opportunities for cyber-related disruptions at ports.
Ports and the maritime industry have been increasingly targeted, with cyberattacks growth rates in triple digits since 2017. The causes of cybersecurity breaches can be intentional or unintentional, such as employee error (e.g. losing a laptop or a storage device retrieved by others, see figure 32). The consequences of such developments are multidimensional and range from data theft to operational disruptions impacting carriers and cargo owners.
Figure 32: Main sources of cyberattacks
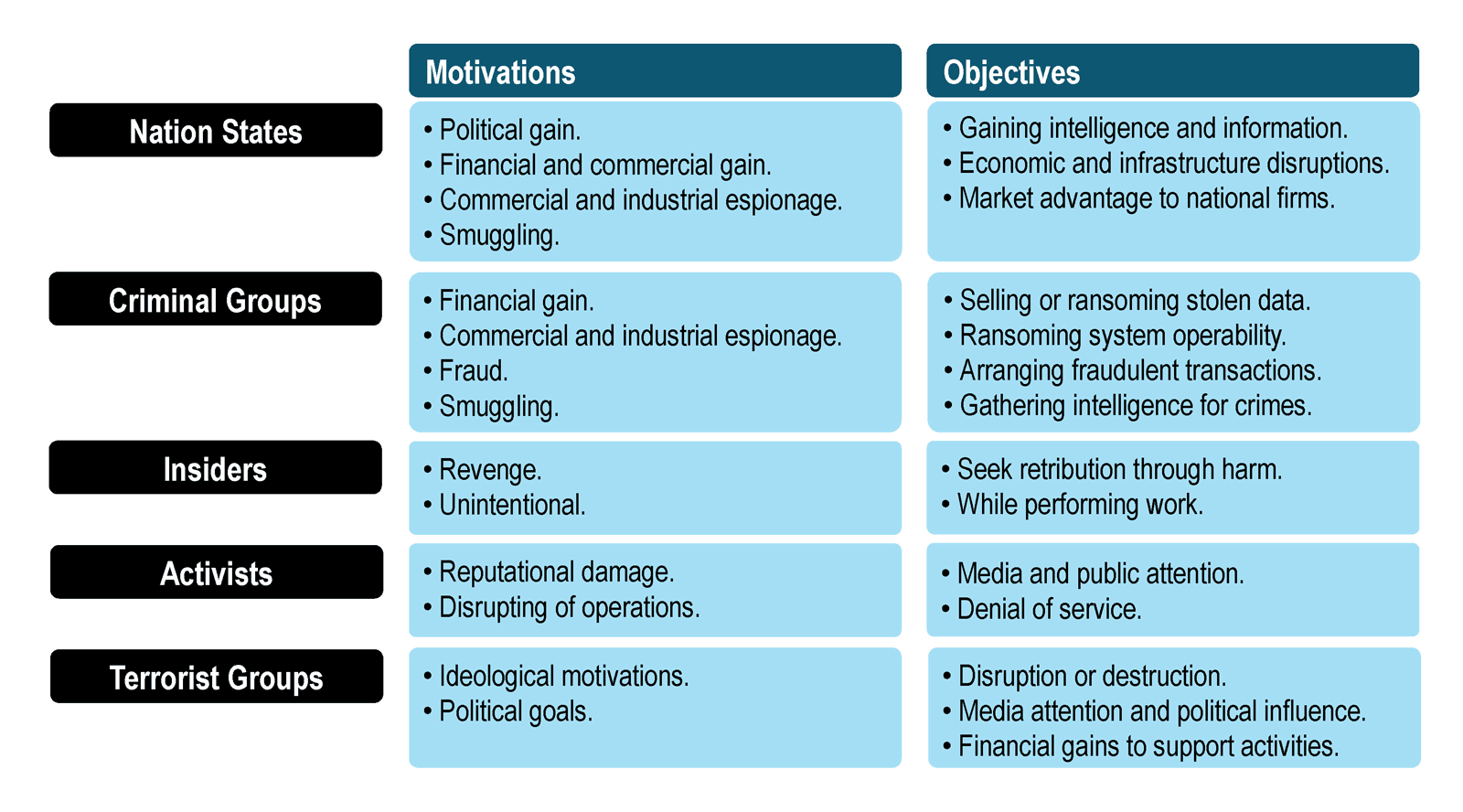
Source: Adapted from IAPH (2021).
Cyberattacks are undertaken by a variety of agents guided by their own motivations and objectives. The core motivation remains financial gains and increasingly undertaken by specialized criminal groups. The use of ransomware is on the rise (box 3); this involves emails which aim to trick at least one recipient within an organization to open an attachment or an embedded link. Once this happens, the malware is activated and propagates through the internal network and infects as many computers as possible. In the case of ransomware, files on infected computers are encrypted, leaving the system unable to function; a message then appears that offers decryption if a payment is made to a specific cryptocurrency wallet.
Other emerging forms of cyberattacks are by activist groups trying to disrupt the IT system of a target organization. This can involve denial of service (DoS) attacks in which a server is overwhelmed with multiple requests. In this case, the motivations are not solely financial, but also aim to damage an organization’s reputation and disrupt its operations. Since cyberattacks continue to evolve in nature, an organization must continuously adapt to new threats, train personnel, and upgrade its IT systems.
Box 3: Petya ransomware cyber-attack on Maersk
In the Summer of 2017, a cyber-attack using “Petya” ransomware affected the Maersk group. Maersk contained the attack but had to shut down multiple systems to prevent the malware from spreading. For a short while, Maersk Line was unable to accept new electronic bookings on its own systems. Its APM terminals division suffered from the effects of the attack at 17 port terminals worldwide, including shutdowns or severe slowdowns for cargo operations at Nhava Sheva (JNPT), Rotterdam, Mobile, Alabama, Port Elizabeth and the Port of Los Angeles. Some terminals had to reserve extra storage space for export containers that were temporarily stranded by APM’s inability to access booking data. The event sent shock waves through the supply chain, causing all parties to re-evaluate their cybersecurity defenses.
Source: Notteboom T. et al (2022).
